CMG basics
The cloud management gateway (CMG) provides a simple way to manage Configuration Manager clients on the internet. By deploying the CMG as a cloud service in Microsoft Azure, you can manage traditional clients that roam on the internet without additional infrastructure. You also don’t need to expose your on-premises infrastructure to the internet.
Deploy the CMG cloud service to Azure.
Add the CMG connection point role.
Configure the site and site roles for the service. Once deployed and configured, clients seamlessly access on-premises site roles regardless of whether they’re on the intranet or internet.
Deployment and operation of the CMG includes the following components:
- The CMG cloud service in Azure authenticates and forwards Configuration Manager client requests to the CMG connection point.
- The CMG connection point site system role enables a consistent and high-performance connection from the on-premises network to the CMG service in Azure. It also publishes settings to the CMG including connection information and security settings. The CMG connection point forwards client requests from the CMG to on-premises roles according to URL mappings.
- The service connection point site system role runs the cloud service manager component, which handles all CMG deployment tasks. Additionally, it monitors and reports service health and logging information from Azure AD. Ensure your service connection point is in online mode.
- The management point site system role services client requests per normal.
- The software update point site system role services client requests per normal.
- Internet-based clients connect to the CMG to access on-premises Configuration Manager components.
- The CMG uses a certificate-based HTTPS web service to help secure network communication with clients.
- Internet-based clients use PKI certificates or Azure AD for identity and authentication.
- A cloud distribution point provides content to internet-based clients, as needed.
Azure resource Manager
Starting in version 1802, you can create the CMG using an Azure Resource Manager deployment. Azure Resource Manager is a modern platform for managing all solution resources as a single entity, called a resource group. When deploying CMG with Azure Resource Manager, the site uses Azure Active Directory (Azure AD) to authenticate and create the necessary cloud resources. This modernized deployment does not require the classic Azure management certificate.
Requirements
- An Azure subscription to host the CMG.
- An Azure administrator needs to participate in the initial creation of certain components, depending upon your design. This person does not require permissions in Configuration Manager.
- At least one on-premises Windows server to host the CMG connection point. You can co-locate this role with other Configuration Manager site system roles.
- The service connection point must be in online mode.
- A server authentication certificate for the CMG.
- If using the Azure classic deployment method, you must use an Azure management certificate but using the Azure Resource Manager deployment model is recommended.
- Other certificates may be required, depending upon your client OS version and authentication model. For more information, see CMG certificates.
- Starting in version 1802, you must configure all CMG-enabled management points to use HTTPS.
- Integration with Azure AD may be required for Windows 10 clients. For more information, see Configure Azure services.
- Clients must use IPv4.
Spécifications
- CMG only supports the management point and software update point roles.
- CMG does not support clients that only communicate with IPv6 addresses.
- Software update points using a network load balancer do not work with CMG.
Cost
- Azure Cloud Services as platform as a service (PaaS)
- A2 V2 VM
- Outbound data transfer: For estimating purposes only, expect approximately 100-300 MB per client per month for internet-based clients. The lower estimate is for a default client configuration. The upper estimate is for a more aggressive client configuration. Your actual usage may vary depending upon how you configure client settings.
Content Storage
- Internet-based clients get Microsoft software update content from Windows Update at no charge. Do not distribute update packages with Microsoft update content to a cloud distribution point, otherwise you may incur storage and data egress costs.
- For any other necessary content, such as applications or third-party software updates, you must distribute to a cloud-based distribution point. Currently, the CMG supports only the cloud-based distribution point for sending content to clients.
CMG Certificates
| Certificat | Name | Type | Target | Details |
| Cloud Management Gateway Certificate
(.PFX) |
ConfigMgr Cloud Management Gateway Certificate | Server authentication certificate | ConfigMgr Cloud Management Gateway installation |
|
| Server Authentication Certificate
(.CER) |
ConfigMgr Web Server Certificate | Server authentication certificate |
|
|
| Client Authentication Certificate
(.CER) |
ConfigMgr Client Certificate |
|
|
|
| Cloud Distribution Point
(.PFX) |
ConfigMgr Cloud-Based Distribution Point Certificate | ConfigMgr Cloud DP installation
Azure Management Certificate |
|
|
| Root Certificate
(.CER) |
All | Validate certification path | ||
| Sub Certificate
(.CER) |
All | Validate certification path |
Set up cloud management gateway for Configuration Manager
Administration Clous Services Cloud Management Gateway
Click Create Cloud Management Gateway
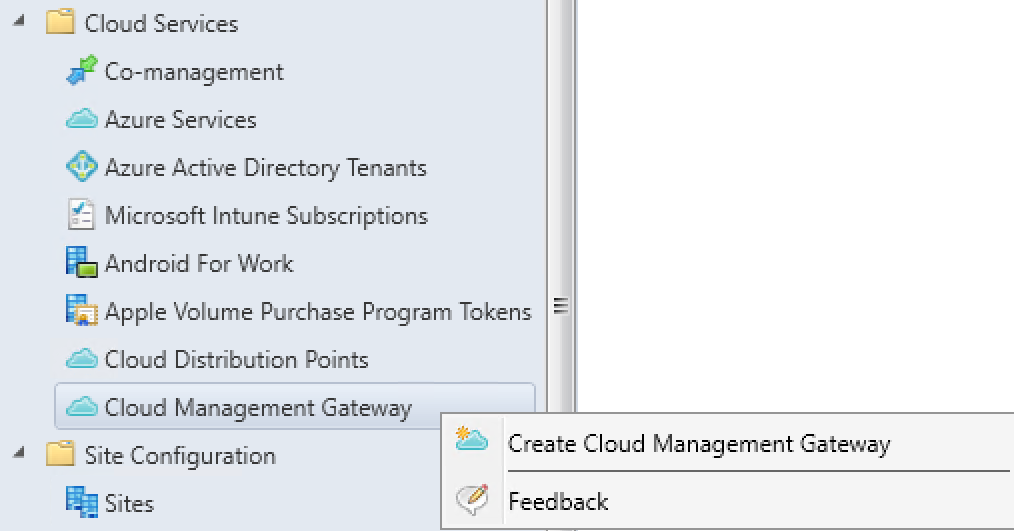
Select Azure Public Cloud, Select Arm deployment, Sign in to your Azure subscription, Click Next
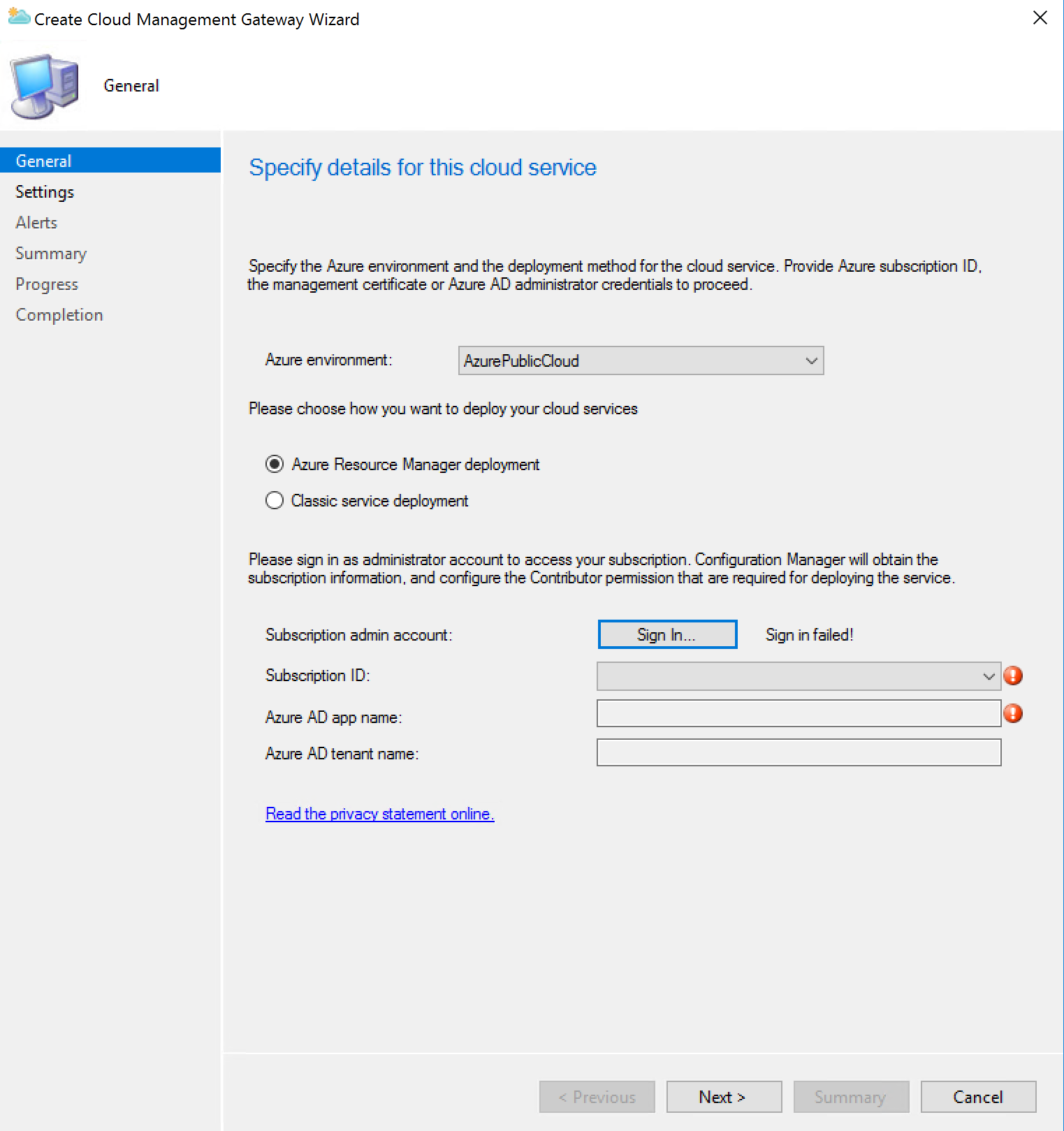
Enter your Azure AD login, Click Next
If you are successfully signed in. Click Next.
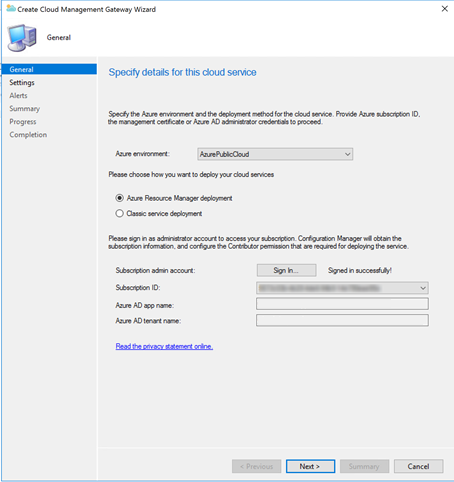
Select the CMG certificate in PFX format. Click Open.
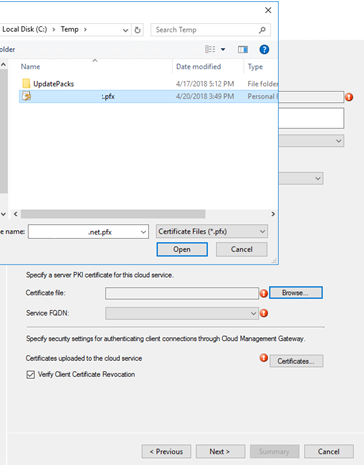
On the Settings page of the wizard, first click Browse and select the .PFX file for the CMG server authentication certificate. The name from this certificate populates the required Service FQDN and Service name fields.
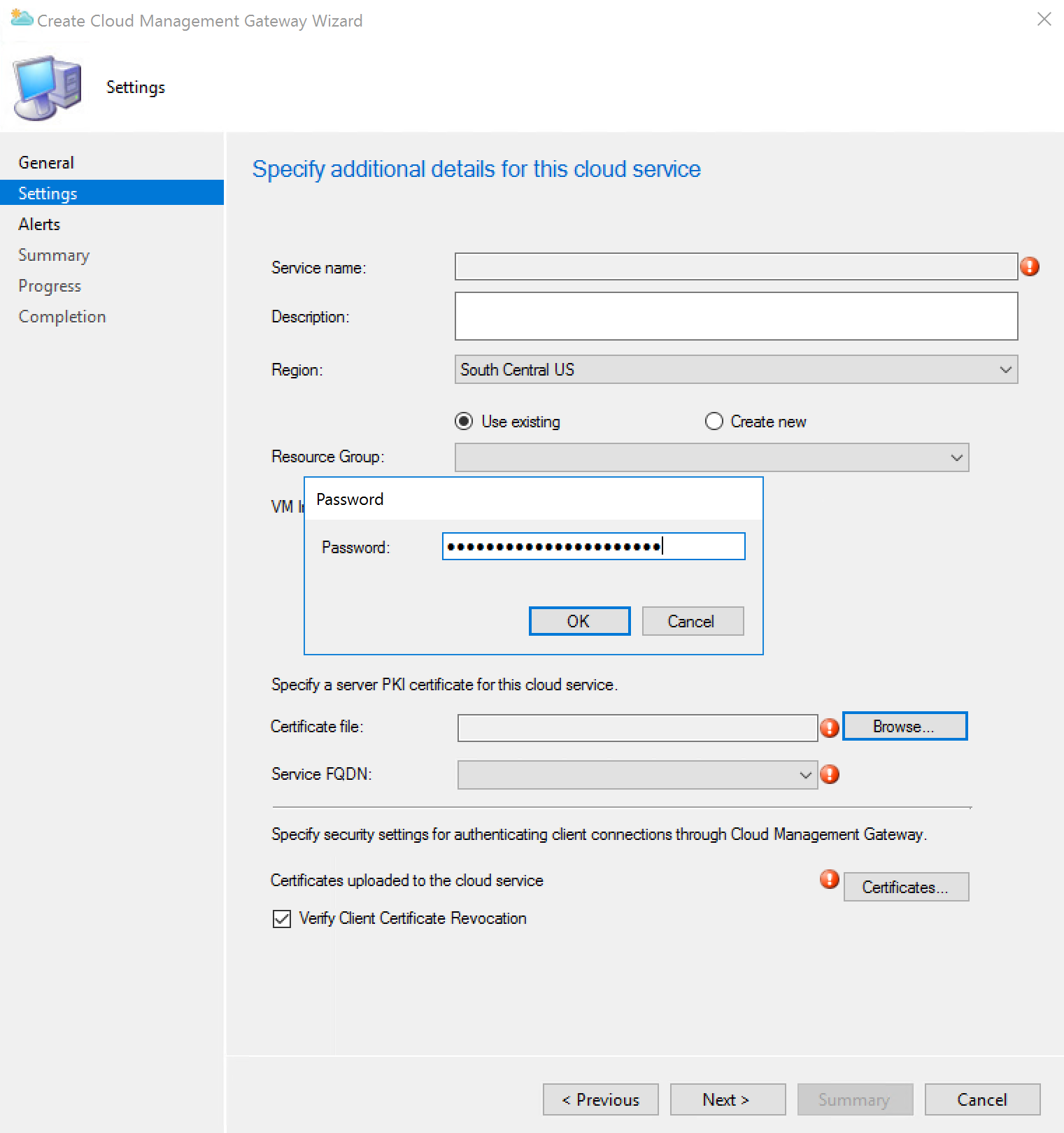
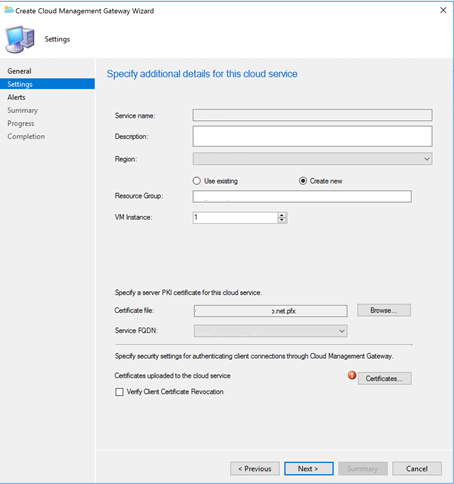
Enter a description Create a new resource group Select CMG deployment region Select VM Instance number.
Untick Verify client certificates Revocation
Click Next.
Import root certificate and sub certificates Click Next
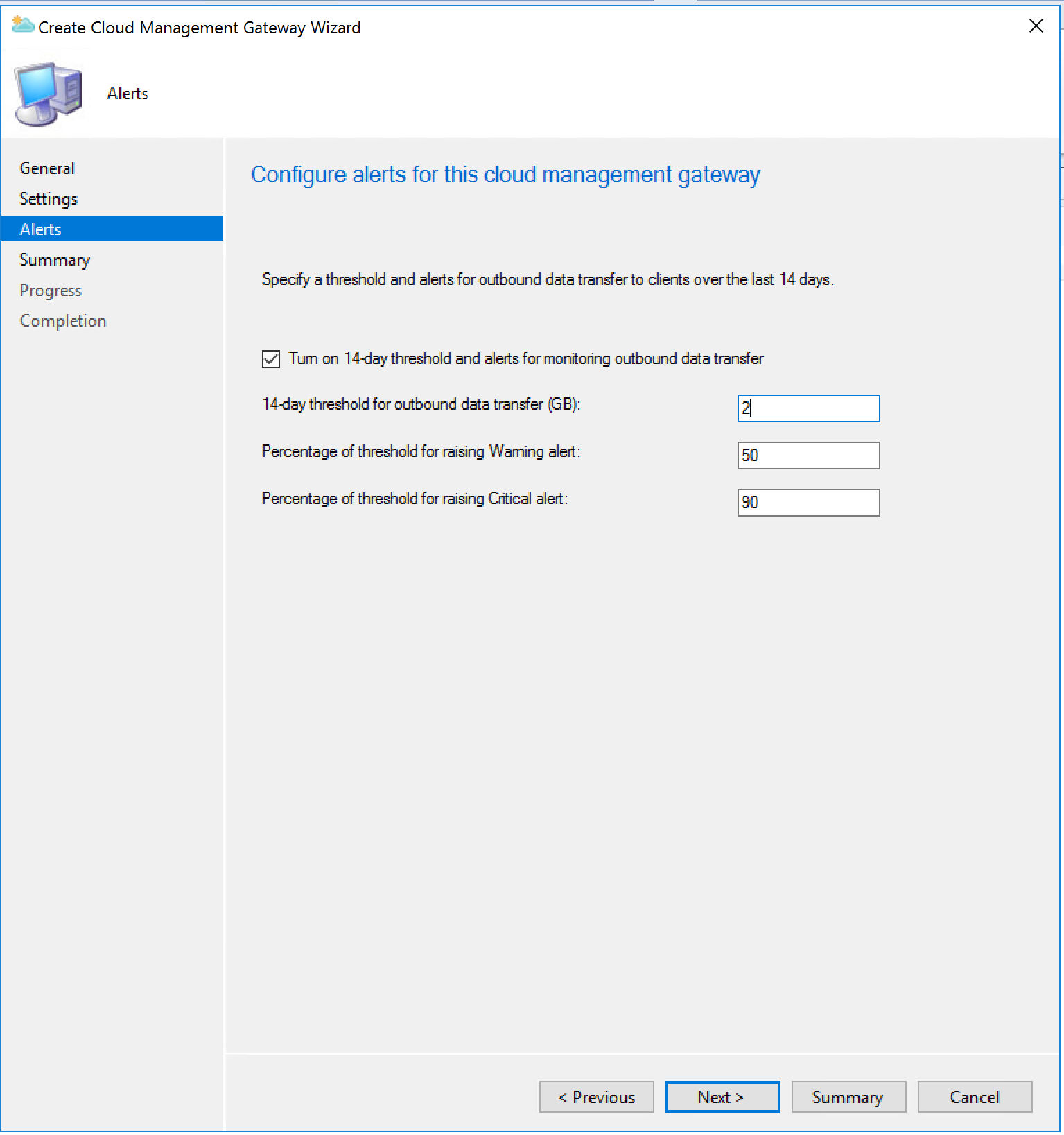
Configure threshold Click Next.
Starting provisionning
![]()
New resource group is creating
![]()
Cloud Service And Storage account
Proxy Service is Running
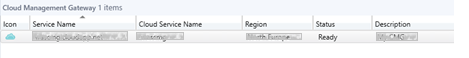
Check if CMG is in ready status in SCCM console
To troubleshoot CMG deployments, use CloudMgr.log and CMGSetup.log. For more information, see Log files.
Configure primary site for client certificate authentication
Administration Site Configuration Sites Primary site Propertie
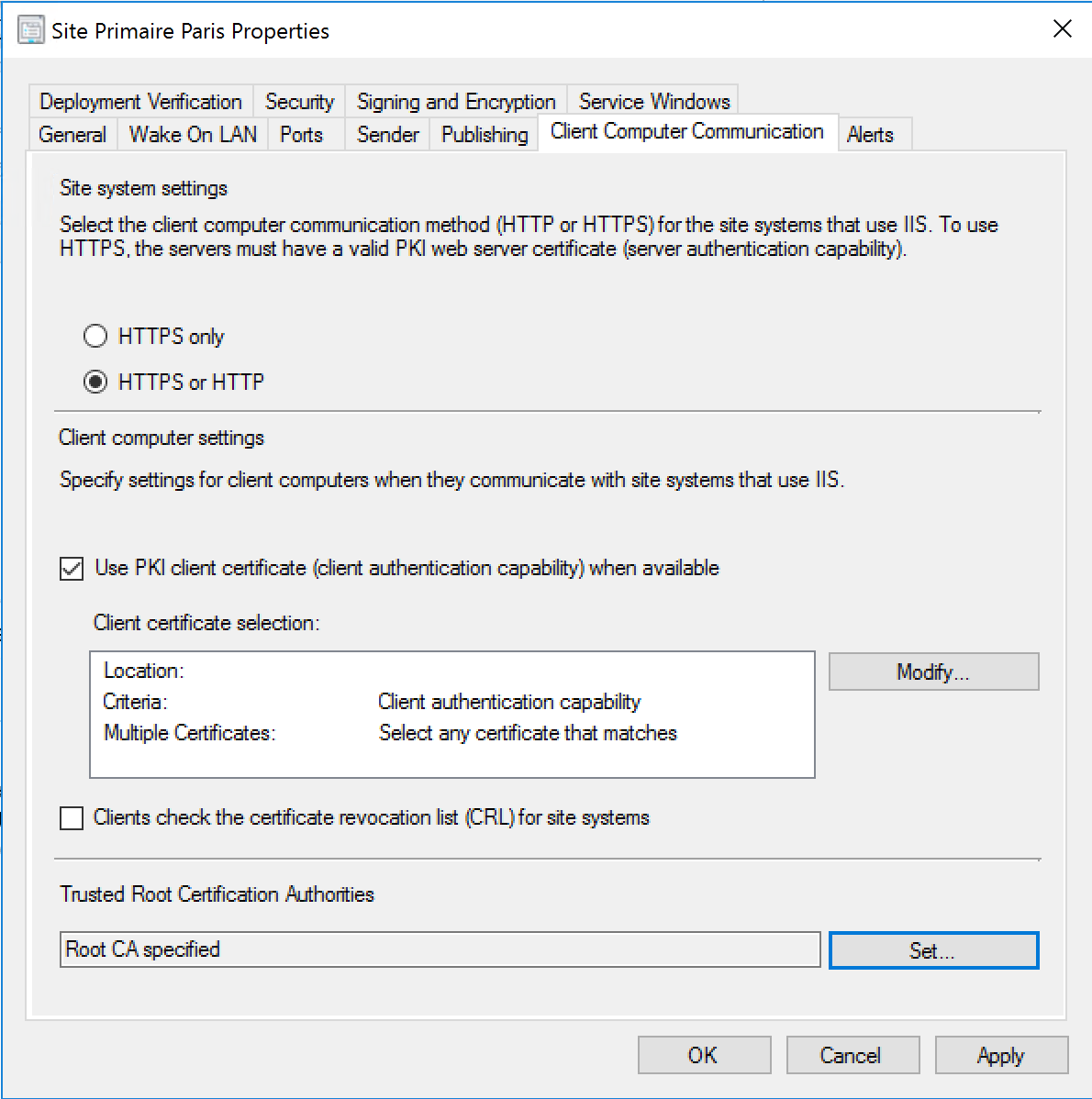
- Select HTTPS or HTTP
- Tick use PKI client certificate
- Untick Clients check the certificate revocation list
- Import root CA
- Click Apply
Add the CMG connection point role
Important :
The CMG connection point must have a client authentication certificate in some scenarios.
![]()
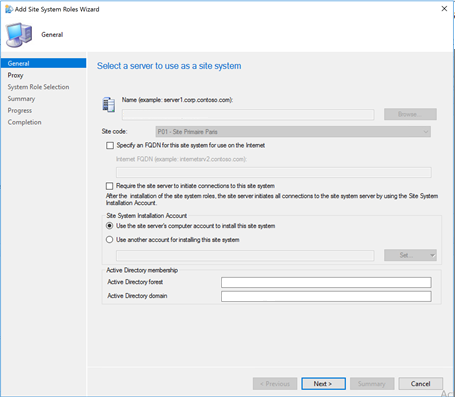
Administration Site Configuration Servers and Site System roles
Select the server
Click Add Site System Role
Click Next
Click Next
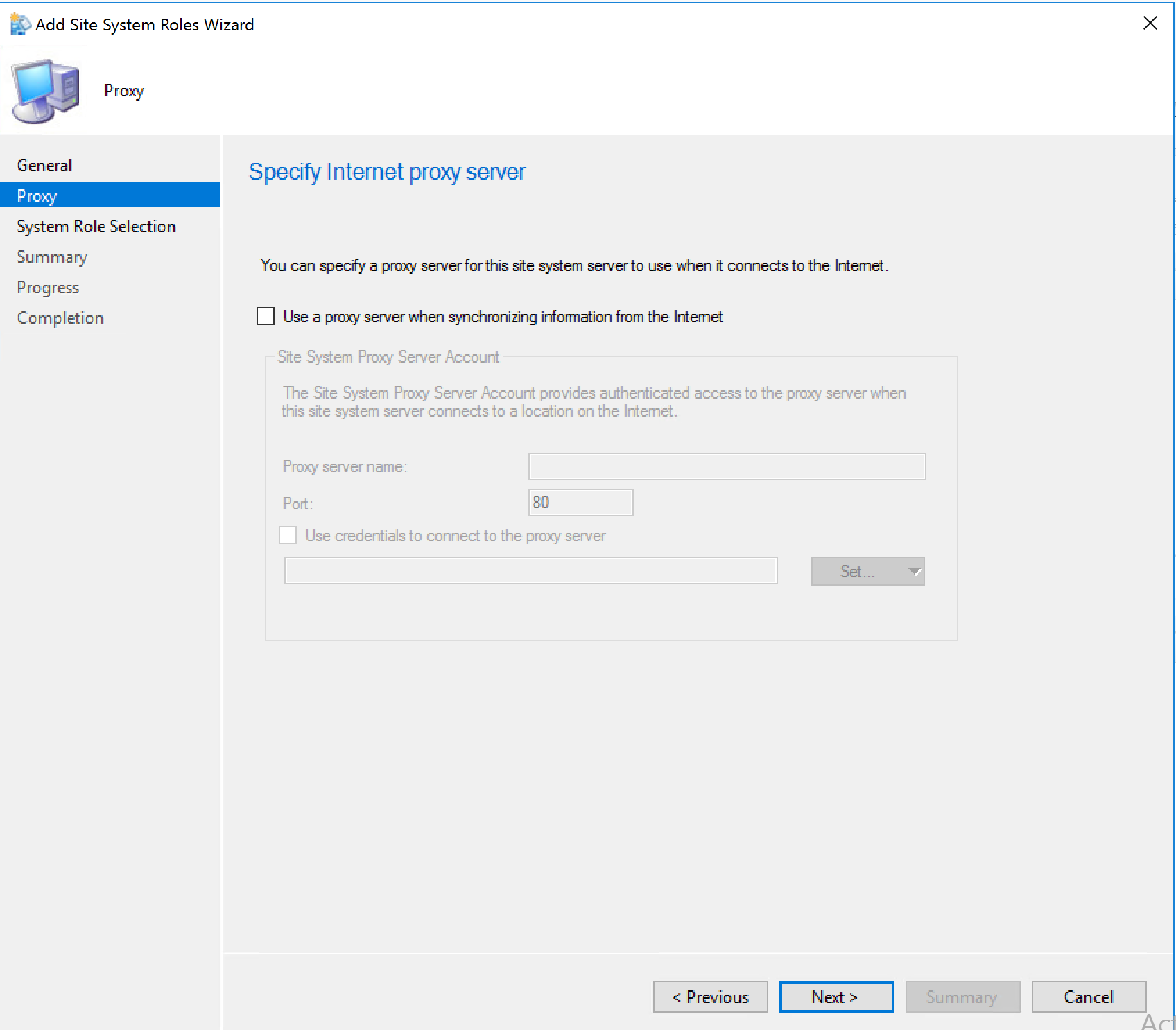
Select Cloud Management gateway connection point Click Next
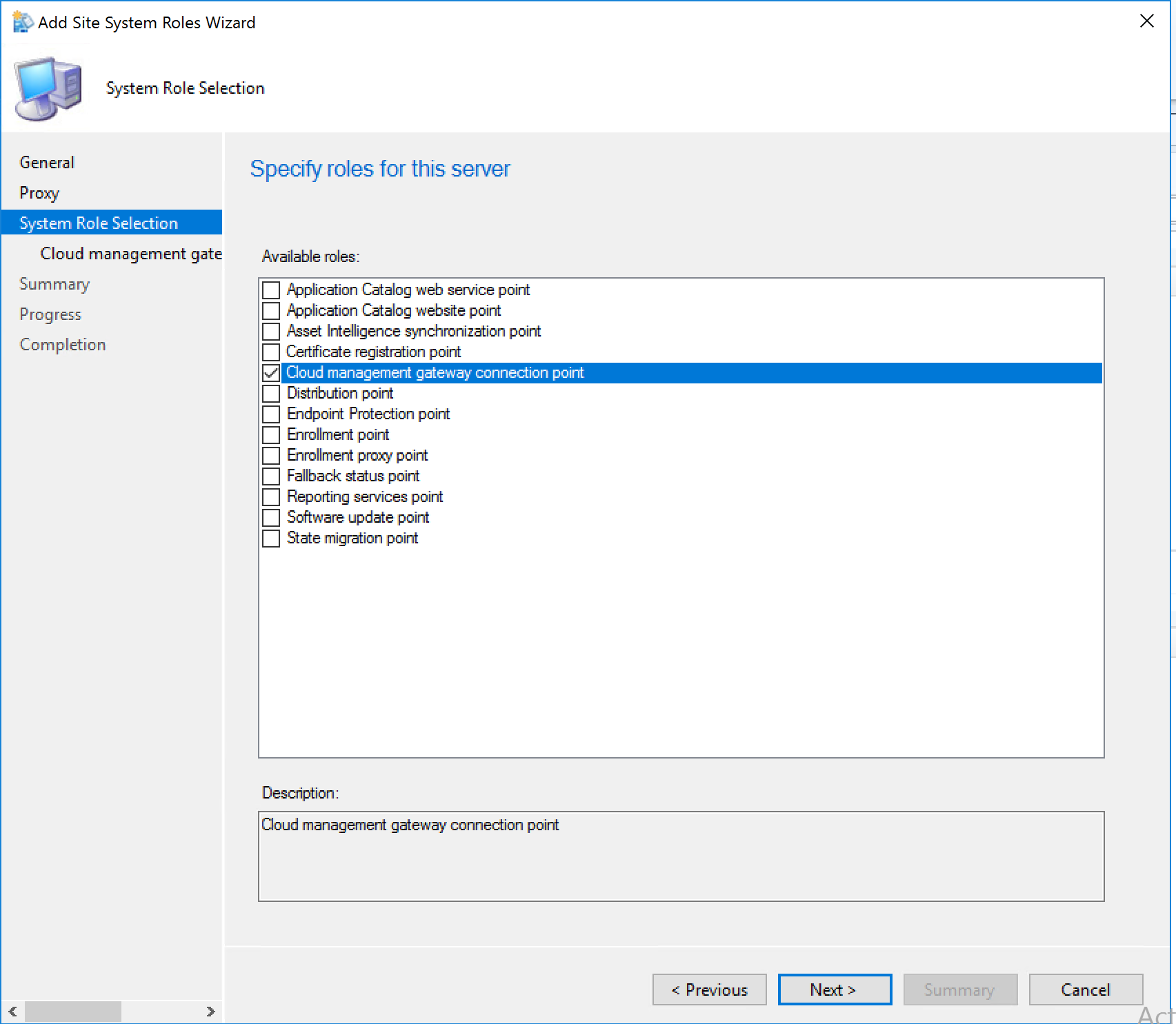
Select the previously deployed CMG in Azure Click Next.

Click Next Click Close.
To troubleshoot CMG service health, use CMGService.log and SMS_Cloud_ProxyConnector.log.
On primary server
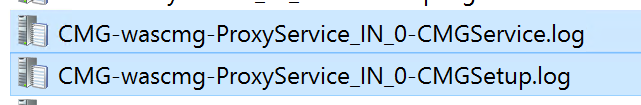
On CMG Server
E:\SMS\Logs
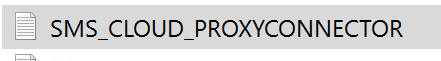
Administration Cloud Services Cloud Management Gateway CMG Name Connection Point tab
CMG Connection point is now connected to azure CMG
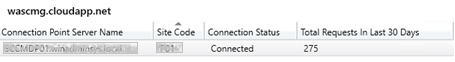
Configure client-facing roles for CMG traffic
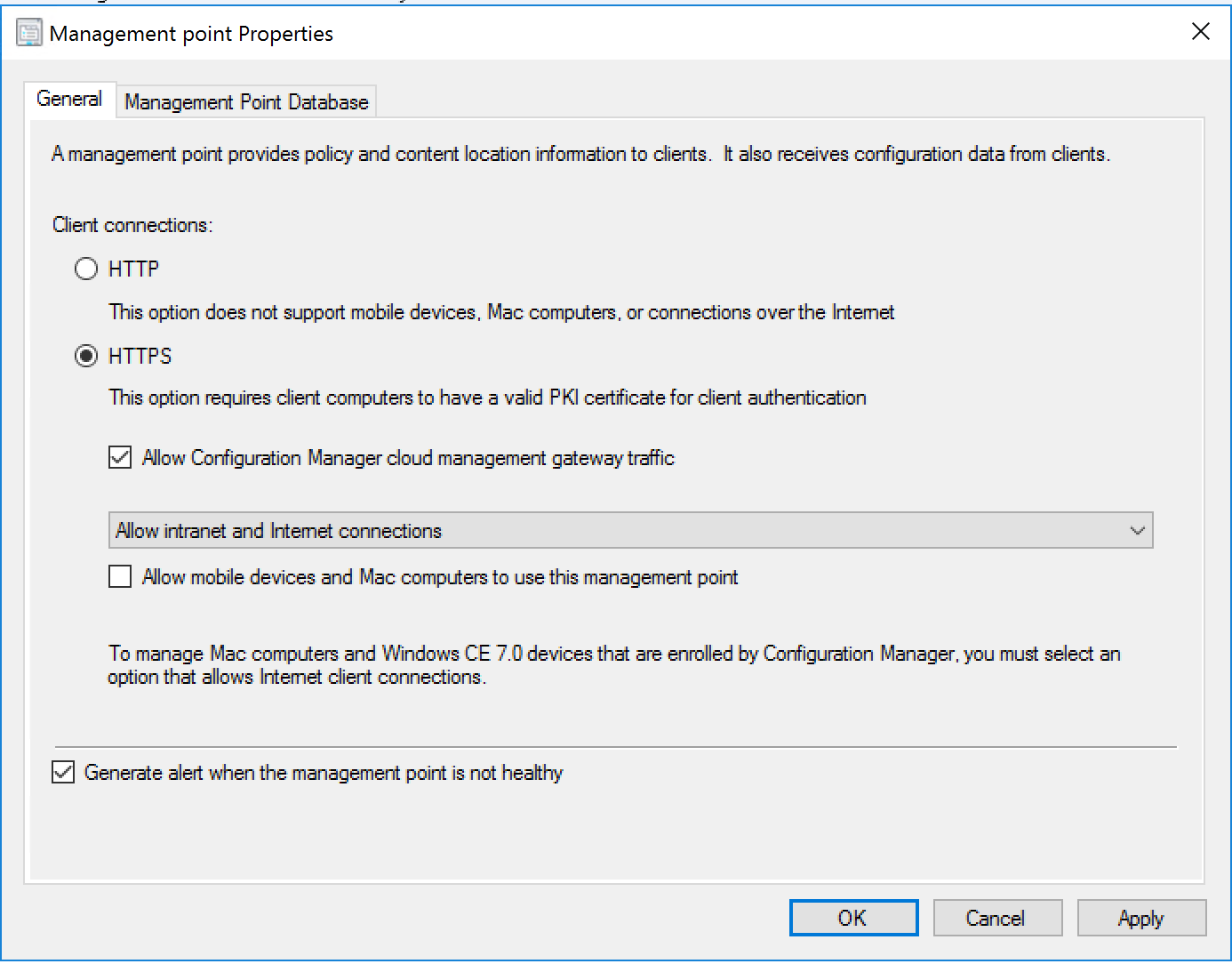
- Select CMG MP Properties
- Click Allow CMG traffic
- IIS Endpoints are now listed in SCCM console
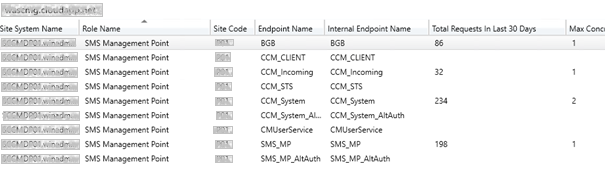
Configure clients for CMG
Note : Clients must be on the intranet to receive the location of the CMG service, unless you install and assign Windows 10 clients using Azure AD for authentication.
By default all clients receive CMG policy. Control this behavior with the client setting, Enable clients to use a cloud management gateway.
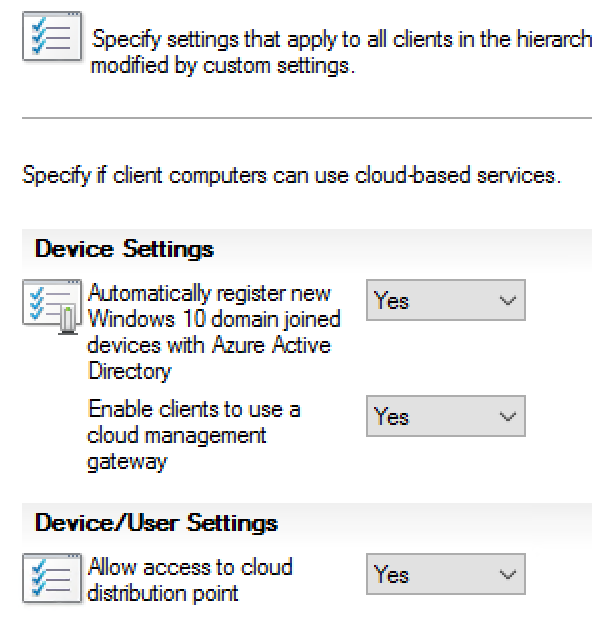
The Configuration Manager client automatically determines whether it’s on the intranet or the internet. If the client can contact a domain controller or an on-premises management point, it sets its connection type to Currently intranet. Otherwise, it switches to Currently Internet, and uses the location of the CMG service to communicate with the site.
To verify that clients have the policy specifying the CMG, open a Windows PowerShell command prompt as an administrator on the client computer, and run the following command:
Get-WmiObject -Namespace Root\Ccm\LocationServices -Class SMS_ActiveMPCandidate | Where-Object {$_.Type -eq « Internet »}
To troubleshoot CMG client traffic, use CMGHttpHandler.log, CMGService.log, and SMS_Cloud_ProxyConnector.log. For more information, see Log files.
Always keep at least one active CMG for internet-based clients to receive updated policy. Internet-based clients can’t communicate with a removed CMG. Clients don’t know about a new one until they roam back to the intranet. When creating a second CMG instance in order to delete the first, also create another CMG connection point.
Only modify the CMG from the Configuration Manager console. Making modifications to the service or underlying VMs directly in Azure is not supported. Any changes may be lost without notice. As with any PaaS, the service can rebuild the VMs at anytime. These rebuilds can happen for backend hardware maintenance, or to apply updates to the VM OS.
Enroll Client Certificate
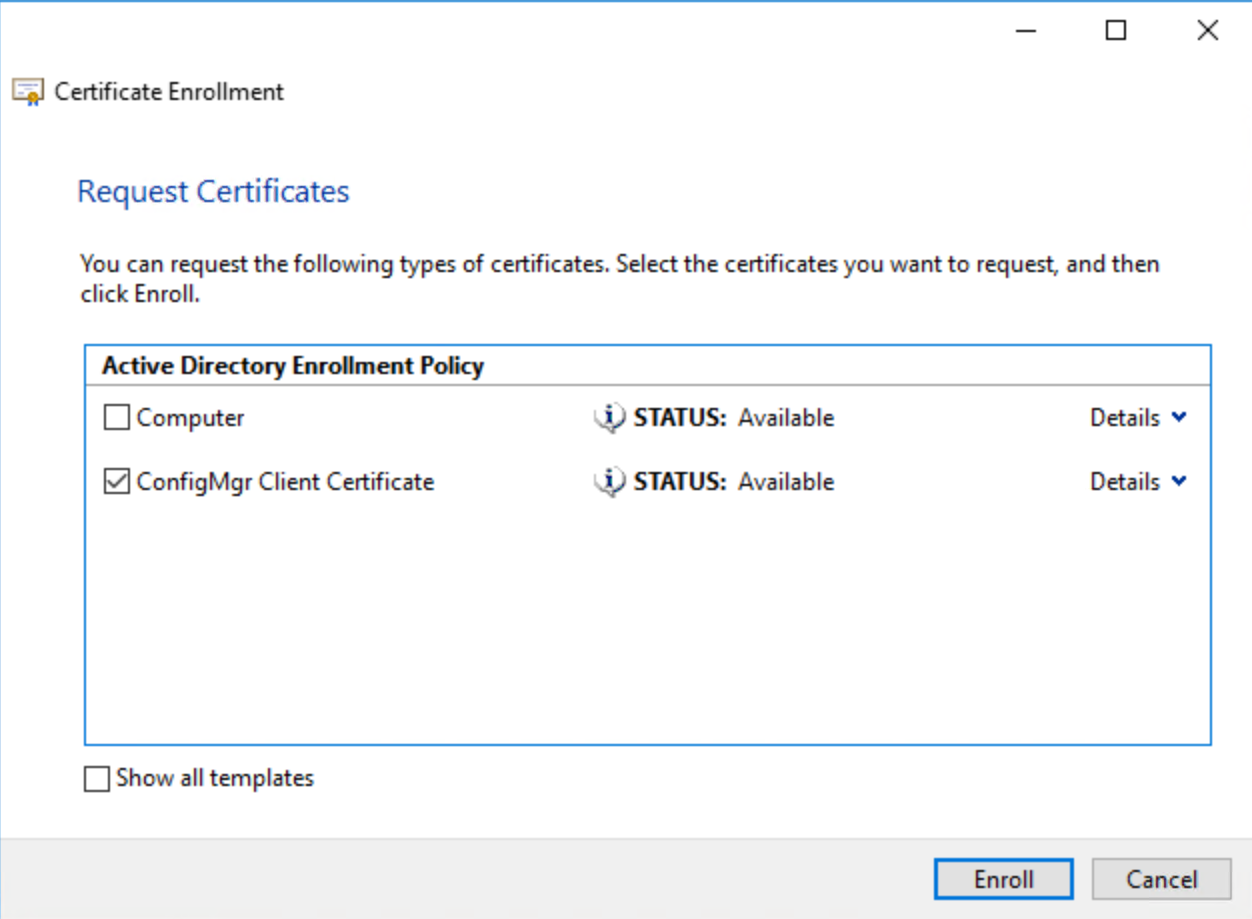
Click Finish
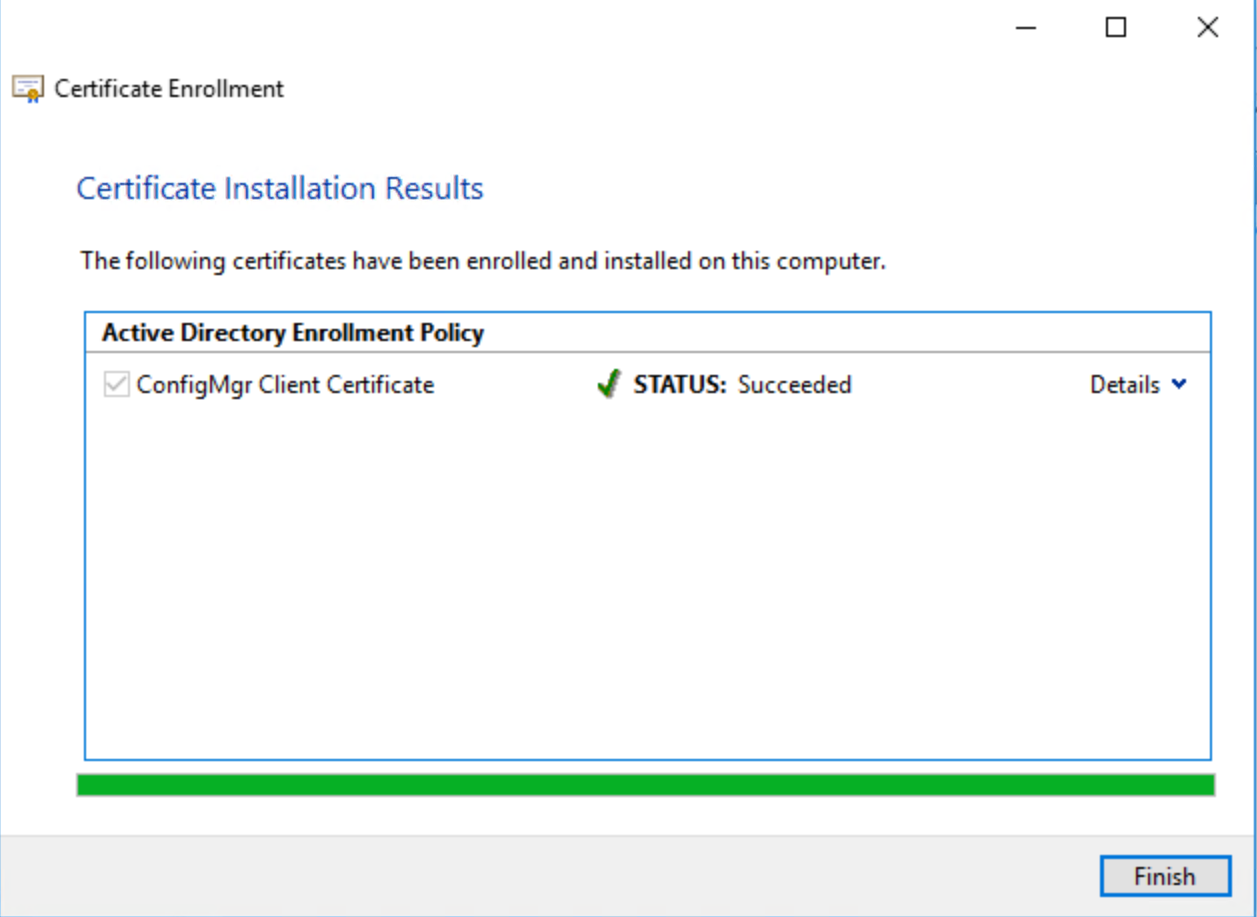

On intranet
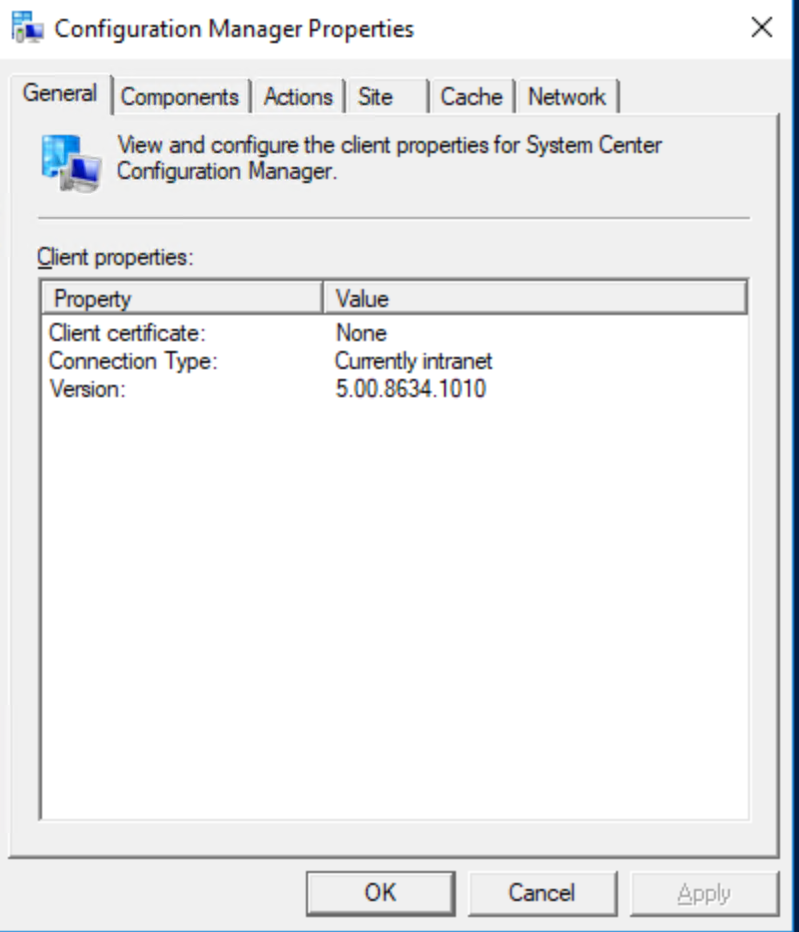
Launch a machine policy retrieval & Evaluation cycle, The client receive the policy with the CMG location.
Connect SCCM client to internet network Client Certificate is now PKI Connection type in Internet
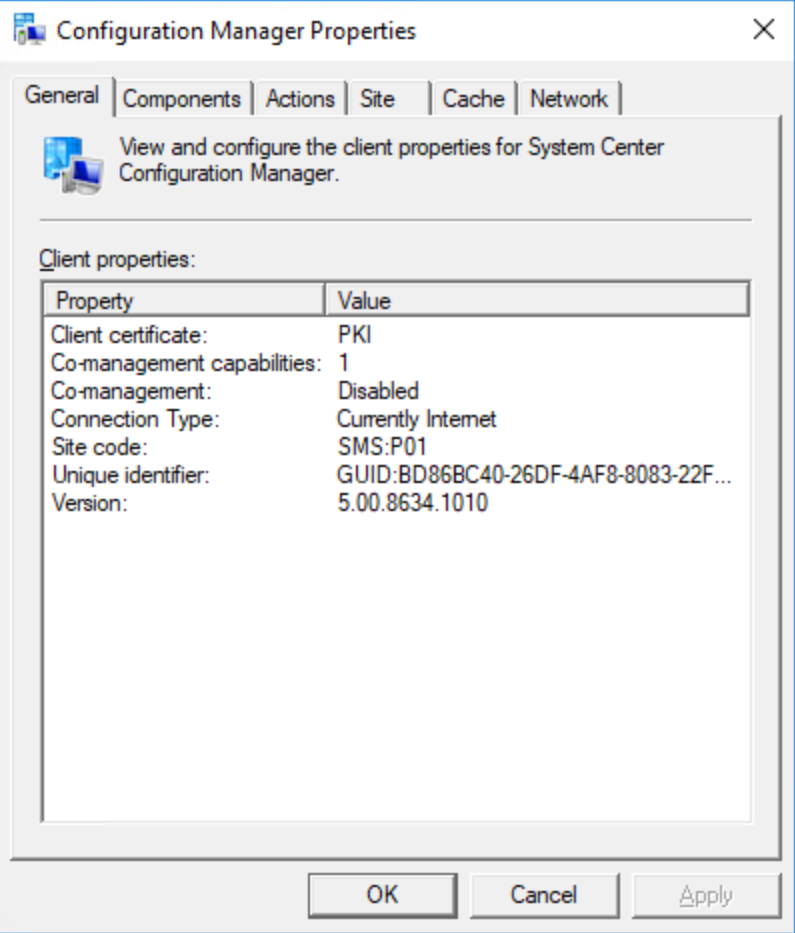
For client troubleshotting, check :
Locationservices.log
CCMMessaging.log
PolicyAgent.log
SCCM client is now connected to the CMG